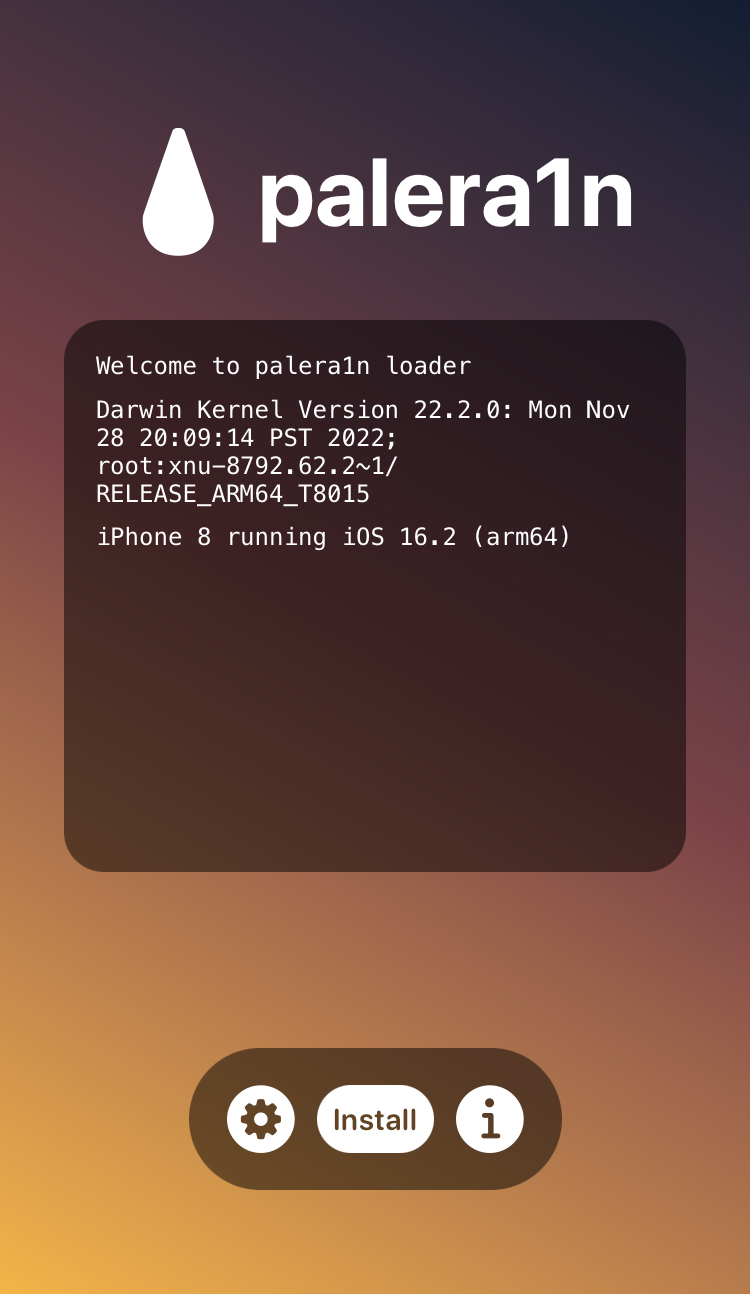
Jailbreak iPhone 8 iOS 16.2 with palera1n and use frida dump to decrypt ipa
Types of Jailbreaks
Tethered
The device must be booted using a computer every time, otherwise it won’t boot at all. This type of jailbreak is uncommon.
e.g.:
- 4039
- blackra1n
Semi-tethered
The device must be jailbroken using a computer every time it’s rebooted, otherwise it will boot in unjailbroken state.
e.g.:
- checkra1n
- palera1n
Semi-untethered
The device must be jailbroken using an app every time it’s rebooted, otherwise it will boot in unjailbroken state. A computer is usually used for the initial installation, but it’s not strictly necessary.
e.g.:
- unc0ver
- Odyssey
- Pangu933
Permasigned semi-untethered
The device must be jailbroken using an app every time it’s rebooted, otherwise it will boot in unjailbroken state. This app will remain signed on the device permanently.
e.g.:
- unc0ver + fugu14
- taurine-permanent
Untethered
The device will stay jailbroken after a reboot, no additional action is required. This type of jailbreak is uncommon.
e.g.:
- Absinthe
- Etason
- Pangu9
What is rootless in palera1n?
Rootless is the future of iOS 15+ jailbreaks. As of now, palera1n has full root support, at the expense of 5-10 GB of storage (or tethered). We aim to switch to rootless, to also bring a smoother experience.
Recover mode and DFU mode
Recover mode
Recovery Mode is a failsafe in iBoot that is used to reflash the device with a new OS, whether the currently installed one is somehow damaged or the device is undergoing an upgrade via iTunes, Finder or Apple Configurator. This is not the same as the recoveryOS available on macOS, watchOS, tvOS and audioOS.
If you can’t update or restore your iPhone or iPod touch You can put your iOS device in recovery mode, then restore it using your computer.
In these situations, you might need to use recovery mode to restore your device:
- Your computer doesn’t recognize your device or says it’s in recovery mode.
- If your screen is stuck on the Apple logo for several minutes with no progress bar.
- You see the recovery mode screen.
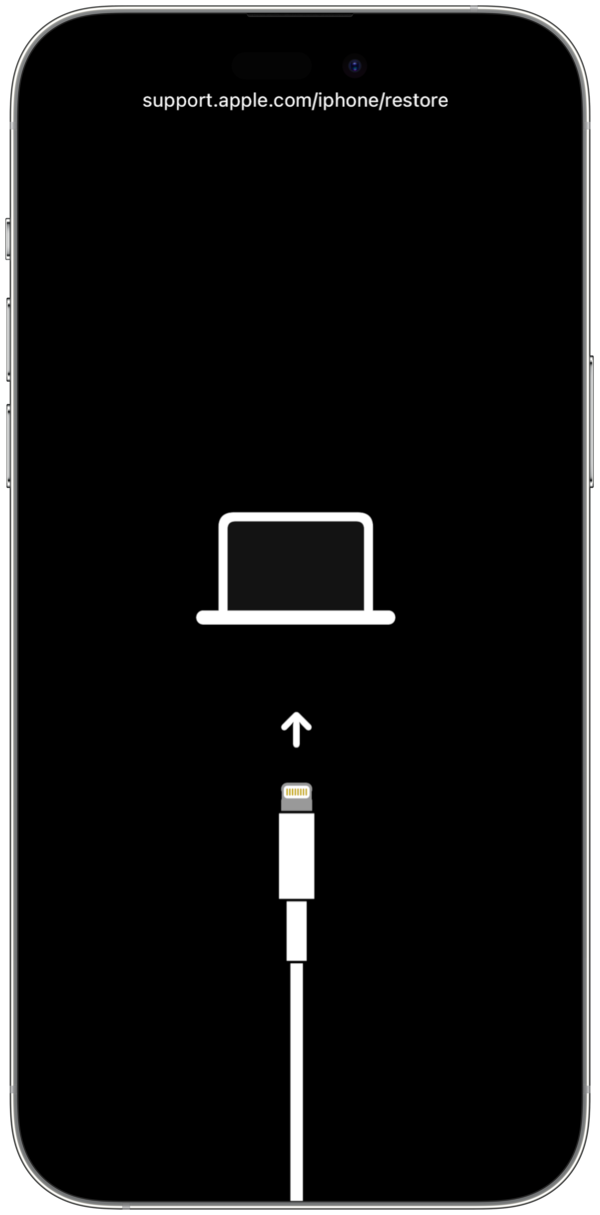
DFU mode
DFU or Device Firmware Upgrade mode allows all devices to be restored from any state. It is essentially a mode where the BootROM can accept iBSS. DFU is part of the SecureROM which is burned into the hardware, so it cannot be removed. On A7+ devices, it generates an ApNonce and recognizes APTickets as well, so even in DFU, it can accept an APTicket.
In DFU mode, phone screen is black.
Enter DFU mode for A11 and newer devices (iPhone 8 and above, iPad Pro 2018, iPad Air 2019, iPad Mini 2019)
- Connect the device to a computer using a USB cable.
- Quick-press the Volume Up button
- Quick-press the Volume Down button
- Hold down the Side button until the screen goes black, then hold down both the Side button and Volume Down button.
- After 5 seconds, release the Side button while continuing to hold down the Volume Down button.
Note: If the Apple logo appears, the Side button was held down for too long.
- Nothing will be displayed on the screen when the device is in DFU mode. Finder will alert you that a device was detected in DFU mode.
How does palera1n works
palera1n is (semi-)tethered checkm8 jailbreak. It requires a checkm8 vulnerable iOS device on iOS 15 or 16 (A8 - A11 or iPhone 6 - iPhone X).
The checkm8 exploit is a bootrom exploit with a CVE ID of CVE-2019-8900 used to run unsigned code on iOS, iPadOS, tvOS, watchOS, bridgeOS, audioOS, and Haywire devices with processors between an A5 and an A11, a S1P and a S3, a S5L8747, and a T2 (and thereby jailbreak it). Jailbreaks based on checkm8 are semi-tethered jailbreaks as the exploit works by taking advantage of a use-after-free in the USB DFU stack.
Jailbreak
palera1n make it easy to jailbreak a vulnerable device, just download repo, run script and following instructions.
$ git clone https://github.com/palera1n/palera1n.git
$ cd palera1n
$ ./palera1n.sh --tweaks 16.2 --semi-tethered
palera1n | Version 1.4.1-main-a6af28a
Made with ❤ by Nebula, Mineek, Nathan, llsc12, Ploosh, and Nick Chan
[*] Waiting for devices
[*] Detected normal mode device
Hello, iPhone10,1 on 16.2!
[*] Switching device into recovery mode...
Telling device with udid xxxx to enter recovery mode.
Device is successfully switching to recovery mode.
[*] Waiting for device in recovery mode
[*] Getting device info...
[*] Press any key when ready for DFU mode
Get ready (0)
Hold volume down + side button (0)
Release side button, but keep holding volume down (6)
[*] Device entered DFU!
[*] Device entered DFU!
[*] Downloading BuildManifest
Version: 9bfdde2b2456181045f74631683fba491d8bf4f2 - 38
libfragmentzip version: 0.64-aaf6fae83a0aa6f7aae1c94721857076d04a14e8-RELEASE
init pzb: https://updates.cdn-apple.com/2022FallFCS/fullrestores/012-73379/0418E94A-C9E6-48E5-9FDF-E61EC6E79312/iPhone_4.7_P3_16.0.3_20A392_Restore.ipsw
init done
getting: BuildManifest.plist
BuildManifest.plist:
download succeeded
[*] Downloading and decrypting iBoot
Version: 9bfdde2b2456181045f74631683fba491d8bf4f2 - 38
libfragmentzip version: 0.64-aaf6fae83a0aa6f7aae1c94721857076d04a14e8-RELEASE
init pzb: https://updates.cdn-apple.com/2022FallFCS/fullrestores/012-73379/0418E94A-C9E6-48E5-9FDF-E61EC6E79312/iPhone_4.7_P3_16.0.3_20A392_Restore.ipsw
init done
getting: Firmware/all_flash/iBoot.d20.RELEASE.im4p
iBoot.d20.RELEASE.im4p:
download succeeded
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Stage: RESET
ret: true
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Stage: SPRAY
ret: true
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Stage: SETUP
ret: true
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Stage: PATCH
ret: true
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Now you can boot untrusted images.
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
Found the USB handle.
[*] Patching and signing iBoot
Version: 7fd877ee7d57a91d2506155752077aad51f896aa-39
main: Starting...
iOS 16 iBoot detected!
getting get_debug_enabled_patch() patch
getting get_sigcheck_patch() patch
applying patch=0x180032c9c : 000080d2
applying patch=0x180032d40 : 000080d2
applying patch=0x1800348b8 : 200080d2
main: Writing out patched file to ibot.patched...
main: Quitting...
000000018001c000[0000000000000300]: iboot_base
0000000180037c64[000000000001bc64]: check_bootmode
00000001800935ee[00000000000775ee]: bootx_str
000000018008e9d0[00000000000729d0]: bootx_cmd_handler
000000018008ea20[0000000000072a20]: go_cmd_handler
0000000180050228[0000000000034228]: zeroBuf
00000001800499f0[000000000002d9f0]: jumpto_bl
0000000180093f36[0000000000077f36]: kc_str
set bootmode: REMOTE_BOOT(1)
bootx -> dorwx
change dorwx_cmd_handler -> 0000000180050228
change go_cmd_handler -> 00000001800502c0
writing sdram_page1
writing load_address
copying payload...
done
jumpto_bl_opcode: 14001a46
kernelcache -> kernelcachd
writing ibot.patched2...
none
[*] Resetting DFU state
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
Found the USB handle.
[*] Booting device
[==================================================] 100.0%
Done!
The device should now boot to iOS
When you unlock the device, it will respring about 30 seconds after
If this is your first time jailbreaking, open the new palera1n app, then press Install
Otherwise, press Do All in the settings section of the app
If you have any issues, please join the Discord server and ask for help: https://dsc.gg/palera1n
Enjoy!
Need follow instructions to let device go to DFU model. You may try several times to make it work. Then script will automatically do remaining work.
Unjailbreak
./palera1n.sh --restorerootfs <iOS version you're on> --tweaks
$ ./palera1n.sh --restorerootfs 16.2 --tweaks
[*] Command ran: ./palera1n.sh --restorerootfs 16.2 --tweaks
palera1n | Version 1.4.1-main-b24a3bd
Made with ❤ by Nebula, Mineek, Nathan, llsc12, Ploosh, and Nick Chan
[*] Waiting for devices
[*] Detected normal mode device
Hello, iPhone10,1 on 16.2!
[*] Switching device into recovery mode...
Telling device with udid xxxx to enter recovery mode.
Device is successfully switching to recovery mode.
[*] Waiting for device in recovery mode
download succeeded
Version: 9bfdde2b2456181045f74631683fba491d8bf4f2 - 38
libfragmentzip version: 0.64-aaf6fae83a0aa6f7aae1c94721857076d04a14e8-RELEASE
init pzb: https://updates.cdn-apple.com/2022FallFCS/fullrestores/012-73379/0418E94A-C9E6-48E5-9FDF-E61EC6E79312/iPhone_4.7_P3_16.0.3_20A392_Restore.ipsw
init done
getting: 098-13133-006.dmg
download succeeded
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Now you can boot untrusted images.
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
Found the USB handle.
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Now you can boot untrusted images.
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
Found the USB handle.
main: Starting...
iOS 16 iBoot detected!
getting get_debug_enabled_patch() patch
getting get_sigcheck_patch() patch
applying patch=0x180032c9c : 000080d2
applying patch=0x180032d40 : 000080d2
applying patch=0x1800348b8 : 200080d2
main: Writing out patched file to work/iBSS.patched...
main: Quitting...
none
main: Starting...
iOS 16 iBoot detected!
getting get_boot_arg_patch(rd=md0 debug=0x2014e wdt=-1 serial=3 ) patch
getting get_debug_enabled_patch() patch
getting get_unlock_nvram_patch() patch
getting get_sigcheck_patch() patch
applying patch=0x180032c9c : 000080d2
applying patch=0x180032d40 : 000080d2
applying patch=0x18001e204 : 000080d2c0035fd6
applying patch=0x18001e25c : 000080d2c0035fd6
applying patch=0x180062378 : 000080d2c0035fd6
applying patch=0x1800348b8 : 200080d2
applying patch=0x180035f78 : d8150d10
applying patch=0x180050230 : 72643d6d64302064656275673d30783230313465207764743d2d312073657269616c3d332000
applying patch=0x18003acb8 : 1f2003d5
main: Writing out patched file to work/iBEC.patched...
main: Quitting...
none
krnl
main: Starting...
main: Detected fat macho kernel
Kernel: Adding AMFI_get_out_of_my_way patch...
get_amfi_out_of_my_way_patch: Entering ...
get_amfi_out_of_my_way_patch: Kernel-8792 inputted
get_amfi_out_of_my_way_patch: Found Internal Error: No cdhash found. str loc at 0xa22ded
get_amfi_out_of_my_way_patch: Found Internal Error: No cdhash found. str ref at 0x12c7734
get_amfi_out_of_my_way_patch: Patching AMFI at 0x12c09d0
main: Writing out patched file to work/kcache.patched...
main: Quitting...
krnl
dtre
rtsc
rdsk
/dev/disk2 /private/tmp/SSHRD
"disk2" ejected.
Reading work/ramdisk.dmg...
IM4P outputted to: work/ramdisk.im4p
Reading work/ramdisk.im4p...
Reading work/IM4M...
Creating Image4...
Image4 file outputted to: sshramdisk/ramdisk.img4
none
[*] Booting ramdisk
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
CPID: 0x8015
Found the USB handle.
Now you can boot untrusted images.
usb_timeout: 5
[IOKit] Waiting for the USB handle with VID: 0x5AC, PID: 0x1227
Found the USB handle.
[*] Testing for baseband presence
[*] Removing Jailbreak
[*] Done! Rebooting your device (if it doesn't reboot, you may force reboot)
SSH
- Install terminal.
- Generate ssh key in /private/etc/ssh as
root.
# cd /private/etc/ssh
# ssh-keygen -A
- Use
iproxy(iproxy - A proxy that binds local TCP ports to be forwarded to the specified ports on a usbmux device) to forward local port (here is 2222) to device.
iproxy [OPTIONS] LOCAL_PORT:DEVICE_PORT [LOCAL_PORT2:DEVICE_PORT2 ...]
iproxy 2222:22
Bind local TCP port 2222 and forward to port 22 of the first device connected via USB.
- ssh to device
ssh root@localhost -p 2222
# default root password is alpine.
To avoid type root password every time. Copy local ssh public key to device ~/.ssh/authorized_keys.
ssh-copy-id -p 2222 -i ~/.ssh/id_ed25519 root@localhost
How encrypted ipa works
Apple’s DRM is known as Fairplay, every time an app is downloaded from the App Store, or Apple’s online service for OTA rollouts, Testflight, they will be encrypted.
The DRM works by placing a special header into the app binary which in turn is encrypted with the Apple specific App Store account public key. At install time, this header is decrypted with the private key stored in your device.
Use otool -l to check cryptid flag to see app is encrypted or not:
otool -l ExampleEncryptedApp.app/ExampleEncryptedApp | grep crypt
cryptoff 417792
cryptsize 4096
cryptid 1 # Encrypted app
otool -l ExampleUnEncryptedApp.app/ExampleUnEncryptedApp | grep crypt
cryptoff 417792
cryptsize 4096
cryptid 0 # Not encrypted app
frida dump to decrypt ipa
git clone https://github.com/AloneMonkey/frida-ios-dump.git
cd frida-ios-dump
pip3 install -r requirements.txt --upgrade
./dump.sh com.example.app
Start the target app com.example.app
Dumping ExampleApp to /var/folders/4w/p521s4wd21s8pcck91vtvby40000gn/T
Troubleshooting
Device not boot after jailbreak
Symptom:
After jailbreak device stay in black screen and not boot.
Solution:
If iPhone isn’t responding, and you can’t turn it off or on, try forcing it to restart.
Steps to force restart iPhone 8 and later models:
- Press and quickly release the volume up button.
- Press and quickly release the volume down button.
- Press and hold the side button.
- When the Apple logo appears, release the side button.
Steps to force restart iPhone 7:
Press and hold both the volume down button and the Sleep/Wake button at the same time. When the Apple logo appears, release both buttons.
Steps to force restart iPhone 6s or iPhone SE (1st generation):
Press and hold both the Sleep/Wake button and the Home button at the same time. When the Apple logo appears, release both buttons.
iproxy: command not found
Symptom:
$ iproxy 2222:22
-bash: iproxy: command not found
Solution:
iproxy is part of libimobiledevice, install it on Mac OS:
brew install libimobiledevice
unable to attach to the specified process
Symptom:
$ ./dump.py com.example.app
Start the target app com.example.app
unable to attach to the specified process
Solution:
Try to launch app manually before run the dump.py.
unable to launch iOS app: The operation couldn’t be completed
Symptom:
$ ./dump.py com.example.app
Start the target app com.example.app
unable to launch iOS app: The operation couldn’t be completed. This system service instance does not support "openApplication"
Solution:
Try to launch app manually before run the dump.py.
Failed to enumerate applications: this feature requires an iOS Developer Disk Image to be mounted; run Xcode briefly or use ideviceimagemounter to mount one manually
Symptom:
Failed to enumerate applications: this feature requires an iOS Developer Disk Image to be mounted; run Xcode briefly or use ideviceimagemounter to mount one manually
Solution:
Here is how to use ideviceimagemounter to mount Developer Disk Image:
$ ideviceimagemounter /Applications/Xcode.app/Contents/Developer/Platforms/iPhoneOS.platform/DeviceSupport/16.2/DeveloperDiskImage.dmg /Applications/Xcode.app/Contents/Developer/Platforms/iPhoneOS.platform/DeviceSupport/16.2/DeveloperDiskImage.dmg.signature
Uploading /Applications/Xcode.app/Contents/Developer/Platforms/iPhoneOS.platform/DeviceSupport/16.2/DeveloperDiskImage.dmg
done.
Mounting...
Done.
Status: Complete
Common Issues
Credit: Those common issues mainly for palera1n are from palera1n discord.
Cannot download apps from App Store
Install Choicy and disable tweak injection into the App Store.
Device boots out of DFU
Method 1
- Make sure your device is in normal or recovery mode.
- Connect your device to your computer.
- Run ./palera1n.sh dfuhelper (use sudo if on Linux).
- Follow the on-screen instructions.
Method 2
- Power off your device.
- Connect it to your computer or a charger.
- As soon as the Apple logo comes on, start doing the DFU mode sequence.
Restore rootfs still keeps app icons
Theres an issue with restoring rootfs where it doesn’t uicache, there is no need to worry, this happens on a couple of other jailbreaks and serve no harm to the user or device.
Pressing “install” on each jailbreak
DO NOT DO THIS. Its not recommended to do this as it would most likely break your jailbreak install. Instead press the gear icon and then press Do All.
Libhooker wants to install
Remove the Chimera and Odyssey repo immediately.
These repos are not meant to be used with palera1n and are able to break your jailbreak if you install anything from them.
panics making loader not appear
You may be encountering some issue related to panics and the loader “not appearing”, on A10+ make sure you have your passcode disabled before jailbreaking. (This does
Daemons crashing on iOS 16.2+
Substitute may cause daemons to crash on iOS 16.2 and above. It’s recommended to downgrade to iOS 16.1.2 or below for now. Or you can try using ElleKit instead, but note that some tweaks don’t yet work with it.
jbinit DIED
Your device may get stuck on a verbose boot screen, and if you look closely you’ll see a “jbinit DIED!” error near the top.
The simplest way to fix this is rm -rf blobs (use sudo if on Linux), then force reboot your device and try to jailbreak again.
For advanced users:
You can also try re-copying the other/rootfs files manually to the device using SSHRD.
Package is in a very bad inconsistent state
You can fix this by running this command in a terminal:
sudo dpkg -r --force-remove-reinstreq PACKAGE_NAME
Could not connect to lockdownd
Try the following steps to fix the issue:
- Unplug and replug your device
- Run idevicepair pair (use sudo on Linux)
- Trust the computer on your device if needed
- Run idevicepair pair again (use sudo on Linux)
Alternatively, you can manually enter recovery mode before starting palera1n.
loader app not appearing
Restore rootfs and rejailbreak with --restorerootfs at the end of your previous command. If neither of these help, make sure you’re waiting enough time (15-30 seconds).
On iPads if other apps don’t appear along side the loader try installing TrollHelper from havoc, and install TrollStore.
Please reinstall Sileo via SSH
If you have AutoSign installed and you reinstall/update Sileo, you’ll get the error message shown in the screenshot. Here’s how to fix it.
- Get access to a terminal by either using SSH or NewTerm
- Type
sudo apt remove autosign. Unless you changed it, the password is alpine. - Once it’s done, type
sudo apt reinstall org.coolstar.sileo. - Try running Sileo again. Feel free to upgrade it if that was what you were planning to do.
- Install AutoSign again.
It should be fixed after these steps.
crash on open
ldid -s /Applications/<appname>.app
procursus
Binaries will need to be resigned by the Procursus Team to fix killed 9, in the meantime, use palera1n strap repo. you can install it from nebula’s repo.
NewTerm not launching
Install NewTerm 2 from https://apt.itsnebula.net/ or get NewTerm3 beta.
“Booted device” but not booted
This may happen when the downloading and patching process is interrupted. Please run ./palera1n.sh clean (use with sudo if on Linux), then try again.
If that doesn’t fix it, it may be caused by an update from the Procursus repo. The quickest way to fix it is ./palera1n.sh --restorerootfs. Alternatively, you can manually restore /usr/libexec/dirs_cleaner from the rootfs snapshot using the sshrd script.
See also
References
- iOS 15.0-16.3 (semi-)tethered checkm8 jailbreak
- Technical analysis of the checkm8 exploit
- frida-ios-dump
- https://support.apple.com/guide/iphone/force-restart-iphone-iph8903c3ee6/15.0
- https://support.apple.com/guide/iphone/force-restart-iphone-iph8903c3ee6/16.0/ios/16.0
- If your iPhone won’t turn on or is frozen
- https://www.theiphonewiki.com/wiki/DFU_Mode
- palera1n on discord
OmniLock - Block / Hide App on iOS
Block distractive apps from appearing on the Home Screen and App Library, enhance your focus and reduce screen time.
DNS Firewall for iOS and Mac OS
Encrypted your DNS to protect your privacy and firewall to block phishing, malicious domains, block ads in all browsers and apps