Splunk != vs. NOT Difference Detail Explained with Examples
Different between
!= and NOT in Splunk search condition, search result and performance impact. How to exclude field from search result?When you want to exclude results from your search you can use
the NOT operator or the != field expression.
However there is a significant difference in the results that are returned from these two methods.
!= vs. NOT Comparison
- Both!= field expression and NOT operator exclude events from your search, but produce different results
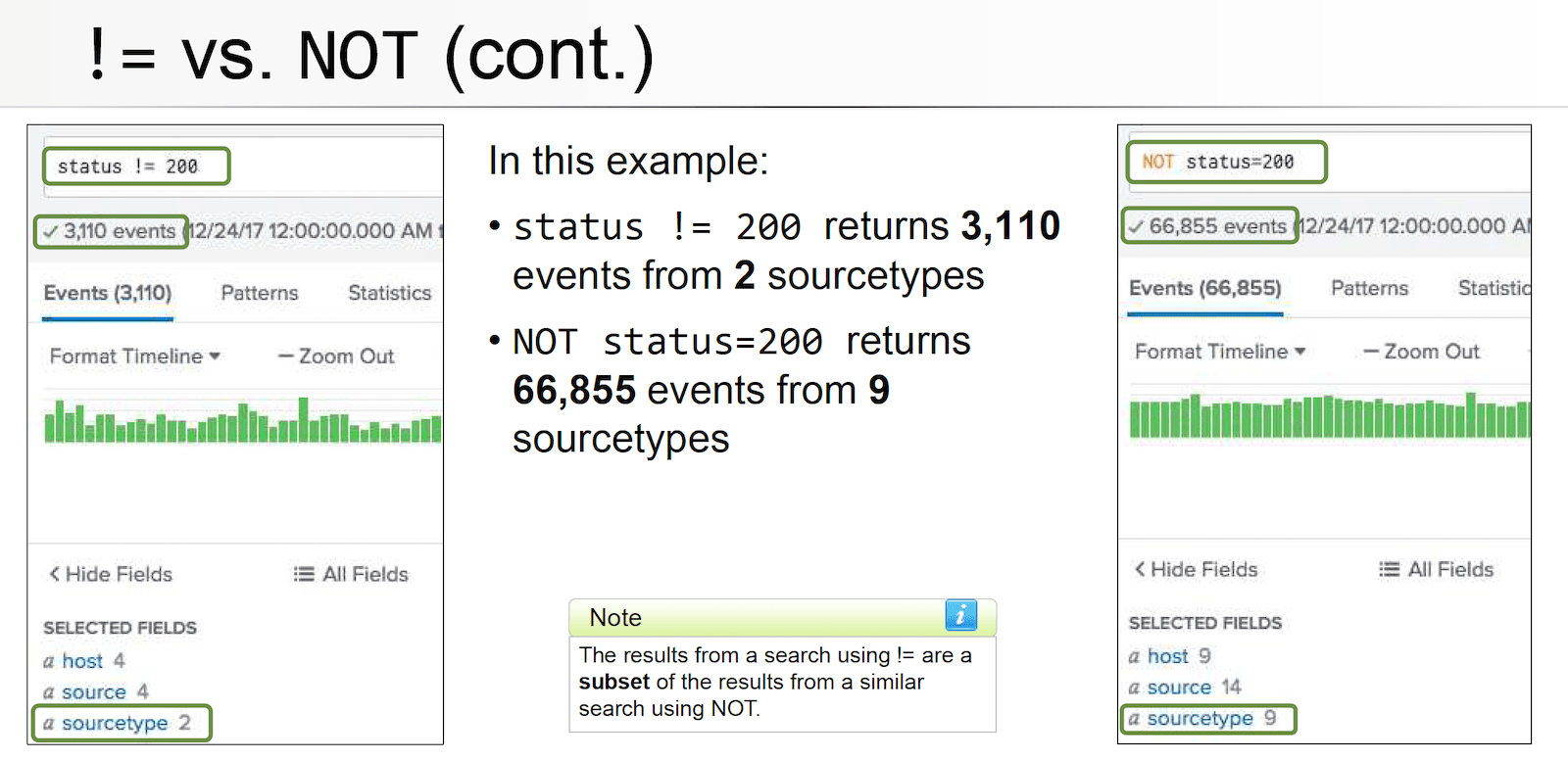
- Example:
status != 200- Returns events where status field exists and value in field doesn’t equal 200
- Example:
NOT status = 200- Returns events where status field exists and value in field doesn’t equal 200 – and all events where status field doesn’t exist
- Does
!=andNOTever yield the same results?- Yes, if you know the field you’re evaluating always exists in the data you’re searching
- For example:
index=web sourcetype=access_combined status!=200index=web sourcetype=access_combined NOT status=200yields same results becausestatusfield always exists inaccess_combinedsourcetype.
Searching with != or NOT is not efficient
Using the != expression or NOT operator to exclude events
from your search results is not an efficient method of filtering events.
The execution cost for a search is actually less when you explicitly
specify the values that you want to include in the search results.
Related pages:
- Troubleshooting Splunk Search Performance by Search Job Inspector
- Splunk Search Best Practices for Better Performance Response Time
- Install Splunk and Forwarder on Linux
Reference
OmniLock - Block / Hide App on iOS
Block distractive apps from appearing on the Home Screen and App Library, enhance your focus and reduce screen time.
DNS Firewall for iOS and Mac OS
Encrypted your DNS to protect your privacy and firewall to block phishing, malicious domains, block ads in all browsers and apps
Ad